This blog post explains how to use VScode IDE for debugging purposes in collaboration with some of the most trend plugins existing out there regarding Android APK dynamic code analysis. This blog post is mainly for Mobile Application Penetration Testers or Security Engineers who need to debug precompiled APKs in order to detect security issues inside the code, inspecting the code flow dynamically. For the purposes of this lab, the InsecureBankv2.apk will be used.
First, the InsecureBankv2.apk will be decompiled using the APKLab plugin. The APKLab plugin can be installed directly to VScode through the use of Extentions as shown at the screenshot below
As also stated at the Extention's page in VScode, APKLab is a plugin that integrates open-source tools to VScode as those listed below, making the tool very effective because it eliminates the need of running these tools outside the IDE, and as such it gives the code analyst the ability to spend more time in debugging the code rather than in the debugging preparation.
- Quark-Engine,
- Apktool,
- Jadx,
- uber-apk-signer,
- apk-mitm
If you want to read more about this amazing plugin you can read the APKLab documentation at the following link https://apklab.surendrajat.xyz
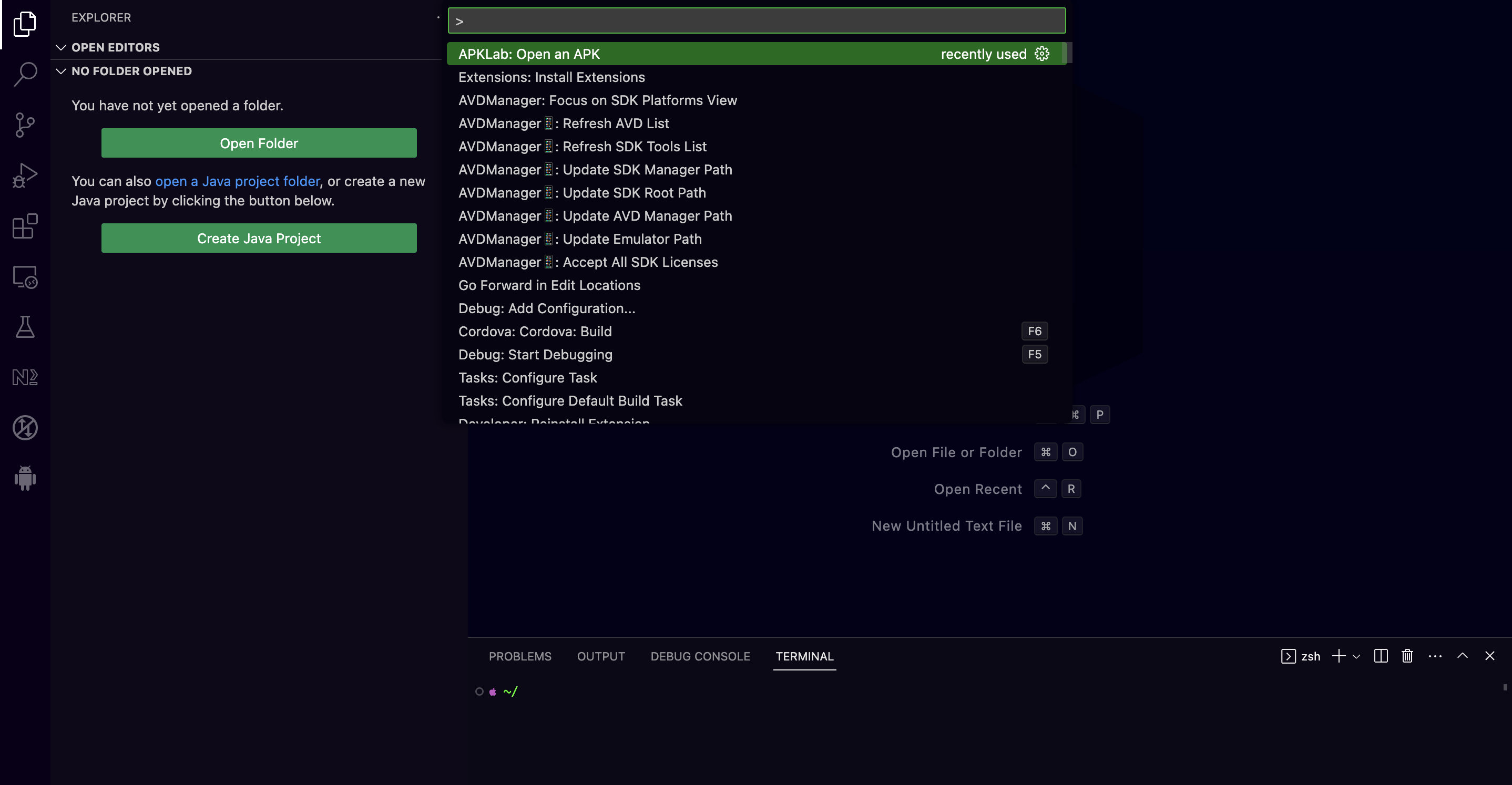
In order to let the APKLab to do its job, we need to open the InsecureBankv2.apk through the VSCode. Then from VSCode Menu, by choosing View->Command Pallete, we can search for the APKLab: Open an APK command as shown at the screenshot below :
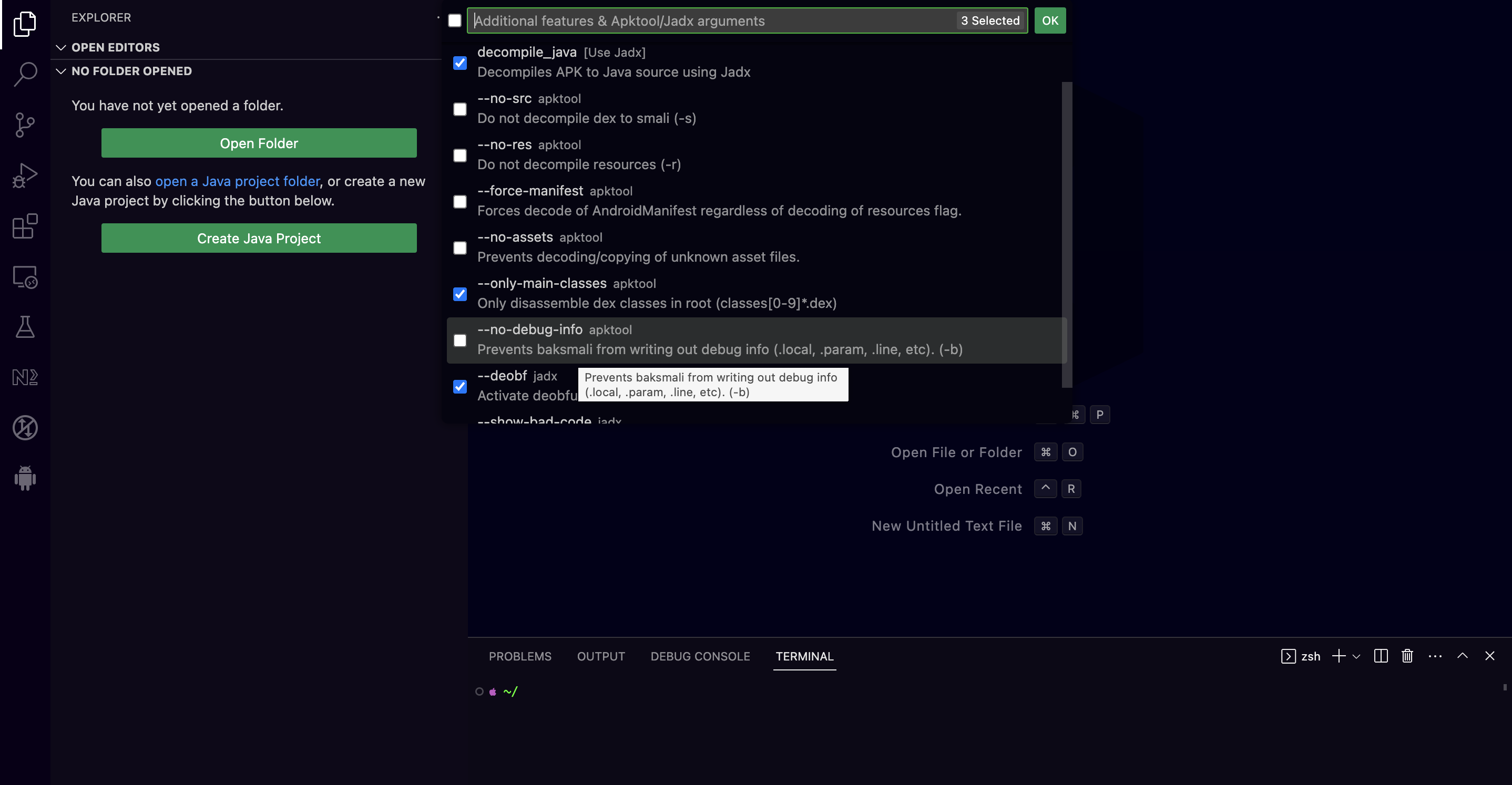
From the Open Folder button as seen at the image above, the InsecureBankv2.apk APK file can be chosen, and from there also several arguments can be selected. The most common arguments are listed below
decompile_java( used for java decompilation ),--only-main-classes( used for disassembling the dex classess ),--deobf( used for deobfuscation )
The screenshot below shows the options we have when we are about to decompile an APK file using the APKLab plugin in VSCode
After pressing ok we can see at the output tab of VSCode, the following lines
------------------------------------------------------------------------- Decoding InsecureBankv2.apk into /Users/xenovas/Documents/InsecureBankv21 ------------------------------------------------------------------------- java -jar /Users/xenovas/.apklab/apktool_2.7.0.jar d /Users/xenovas/Documents/InsecureBankv2.apk -o /Users/xenovas/Documents/InsecureBankv21 I: Using Apktool 2.7.0 on InsecureBankv2.apk I: Loading resource table... I: Decoding AndroidManifest.xml with resources... I: Loading resource table from file: /Users/xenovas/Library/apktool/framework/1.apk I: Regular manifest package... I: Decoding file-resources... I: Decoding values */* XMLs... I: Baksmaling classes.dex... I: Copying assets and libs... I: Copying unknown files... I: Copying original files... Decoding process was successful ------------------------------------------------------------------------------------- Decompiling InsecureBankv2.apk into /Users/xenovas/Documents/InsecureBankv21/java_src ------------------------------------------------------------------------------------- /Users/xenovas/.apklab/jadx-1.4.6/bin/jadx --deobf -r -q -v -ds /Users/xenovas/Documents/InsecureBankv21/java_src /Users/xenovas/Documents/InsecureBankv2.apk Decompiling process was successful
As seen from the output above, APKLab first uses the apktool version 2.7.0 in order to decode the android app into smali code and then uses jadx tool version 1.4.6 in order to perform the actual decompilation of the provided code in java
jadx --deobf -r -q -v -ds /Users/xenovas/Documents/InsecureBankv21/java_src /Users/xenovas/Documents/InsecureBankv2.apk
From this point the InsecureBankv2.apk APK file has been decompiled and the code can be now analysed statically. The following screenshot shows the decompiled code as seen from the Explorer tab of VSCode
Nevertheless, as mentioned before, this lab is about to provide instructions on how to setup an APK debugger on VSCode in order to debug a decompiled .apk file. Thus, the next steps are about to show how to setup a debugger in order to accomplish this task.
The actual structure of the decompiled APK can be seen below
InsecureBankv2 ├── AndroidManifest.xml ├── apktool.yml ├── java_src ├── original ├── res └── smali
From the tree view above, all the source code is located at the java_src folder. Furthermore, the decompiled dex classes that are directly related with the application are also located at the path depicted by the relevant running process on the android device. The AndroidManifest.xml describes essential information about the application to the Android build tools, the operating system, as well as the Google Play. Furthermore, the main resource files such as XML files used to define attribute animations, or other XML files containing drawables, etc., are placed into the res folder. Also the smali folder contains the decompiled code in smali which is also very intresting location as the smali code can be modified and patched in order to alter the application's behaviour. Finally, the original folder is the original AndroidManifest.xml file. The apktool.yml contains the configuration needed from the APKLab plugin in order to execute the apktool along with the relevant options provided by the developer. The apktool can be used to compile or decompile the APK.
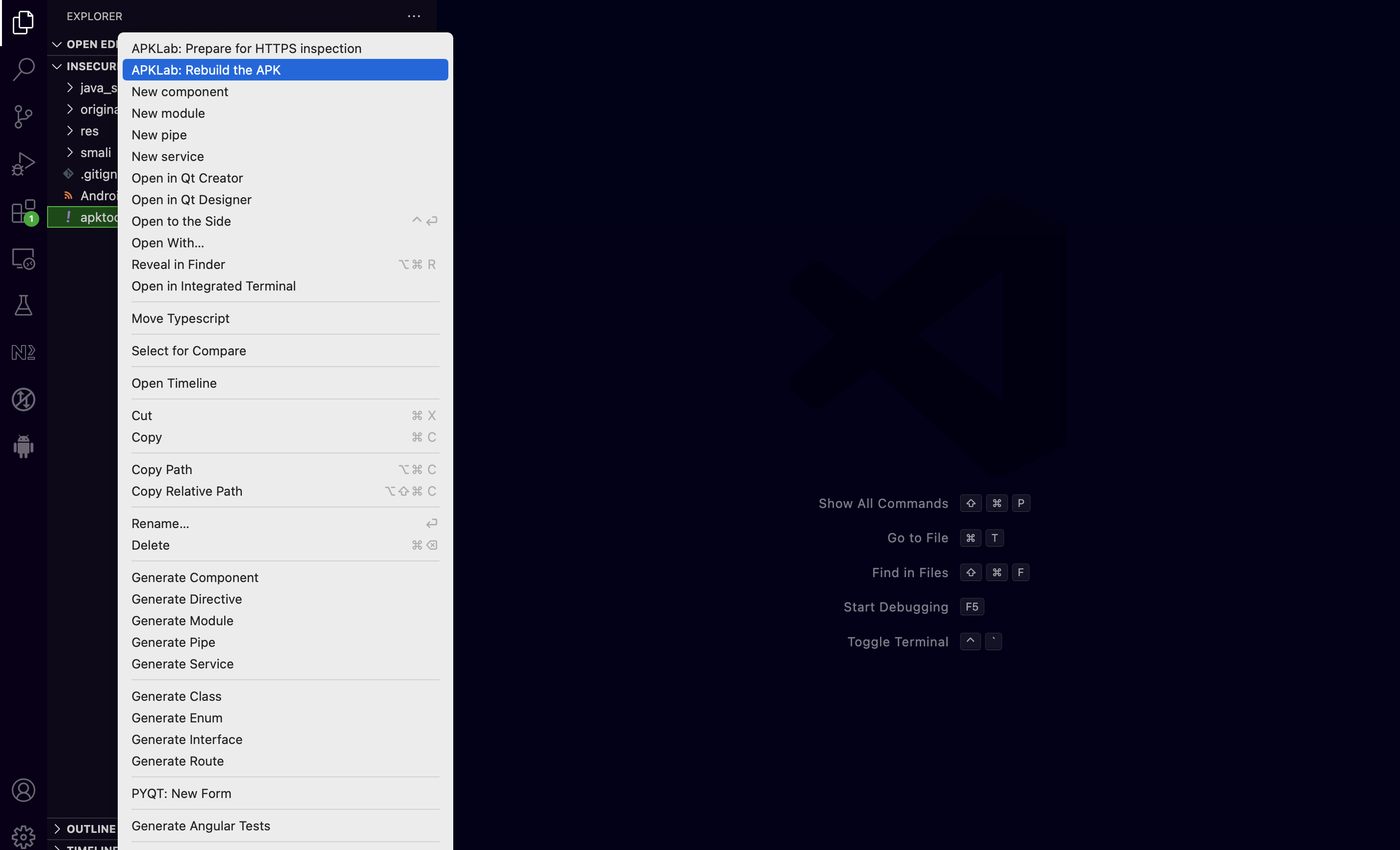
At this point we will rebuild the APK using the apktool in order to recompile it with debug mode enabled. This could be easily accomplished by using the APKLab plugin. The following screenshot shows the APKLab: Rebuild the APK option when right clicking on apktool.yml
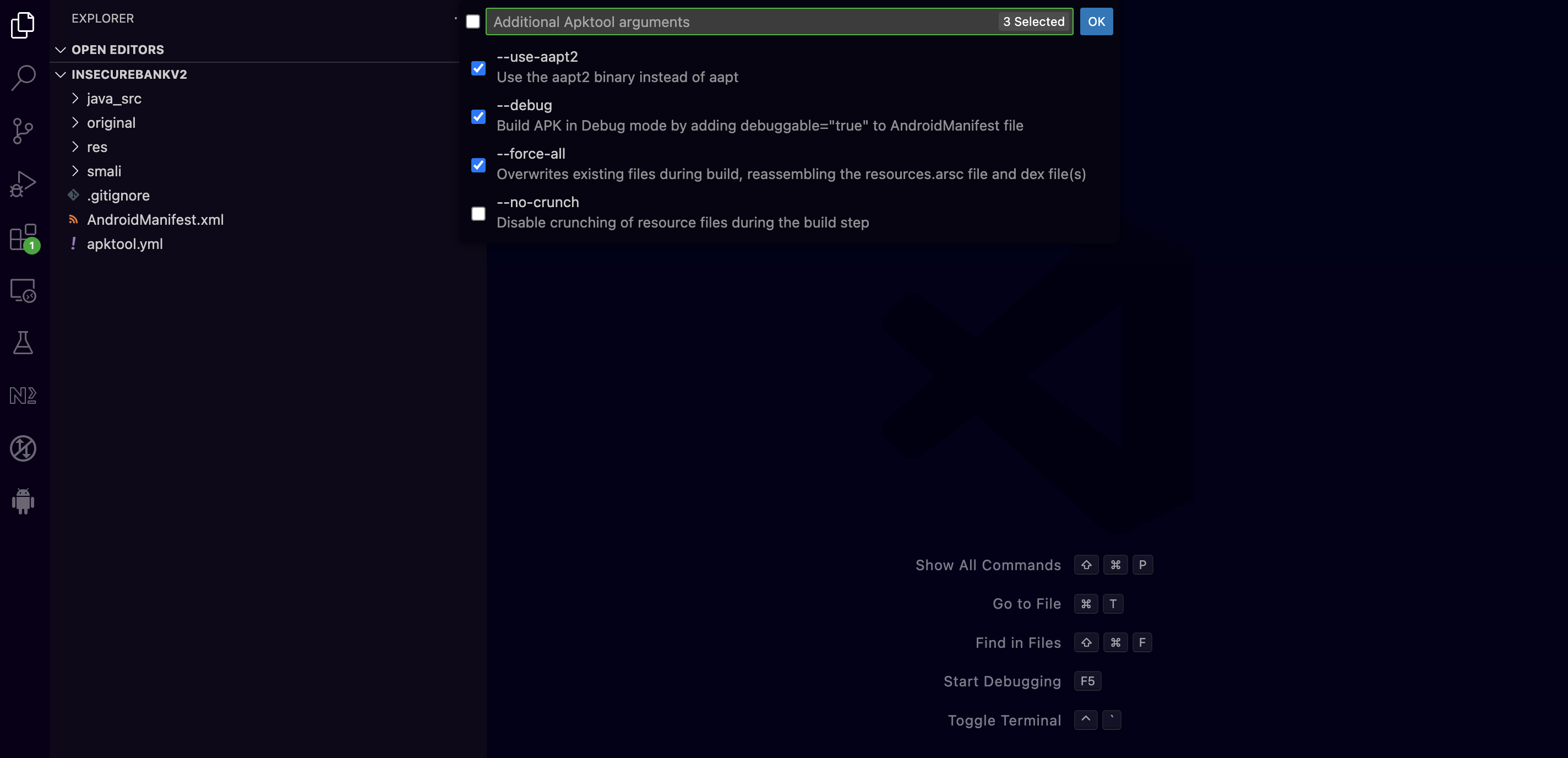
The following screenshot shows the apktool optional arguments as seen from the command palette on VSCode
In order to rebuild the InsecureBankv2.apk we run the apktool by right clicking on the apktool.yml file from inside the VSCode IDE
After rebuilding the InsecureBankv2.apk the following output should be shown
------------------------------------------------------
Rebuilding InsecureBankv2.apk into InsecureBankv2/dist
------------------------------------------------------
java -jar /Users/xenovas/.apklab/apktool_2.7.0.jar b /Users/xenovas/Documents/InsecureBankv2 --use-aapt2 --debug --force-all
I: Using Apktool 2.7.0
I: Smaling smali folder into classes.dex...
I: Building resources...
I: Using aapt2 - setting 'debuggable' attribute to 'true' in AndroidManifest.xml
I: Building apk file...
I: Copying unknown files/dir...
I: Built apk into: /Users/xenovas/Documents/InsecureBankv2/dist/InsecureBankv2.apk
Rebuilding process was successful
----------------------------------------------
Signing InsecureBankv2/dist/InsecureBankv2.apk
----------------------------------------------
java -jar /Users/xenovas/.apklab/uber-apk-signer-1.2.1.jar -a /Users/xenovas/Documents/InsecureBankv2/dist/InsecureBankv2.apk --allowResign --overwrite
source:
/Users/xenovas/Documents/InsecureBankv2/dist
zipalign location: BUILT_IN
/var/folders/wt/dwh1ny455fv8rl8_9j6w24c00000gp/T/uapksigner-11340919931074350973/mac-zipalign-29_0_25123199226427879560.tmp
keystore:
[0] 161a0018 /private/var/folders/wt/dwh1ny455fv8rl8_9j6w24c00000gp/T/temp_56956349993093176_debug.keystore (DEBUG_EMBEDDED)
01. InsecureBankv2.apk
SIGN
file: /Users/xenovas/Documents/InsecureBankv2/dist/InsecureBankv2.apk (3.26 MiB)
checksum: b8221fa10684c0bb40df7b95ea5a5066a8e36a4a359c4b49f19e3c9e02529ac2 (sha256)
- zipalign success
- sign success
VERIFY
file: /Users/xenovas/Documents/InsecureBankv2/dist/InsecureBankv2.apk (3.3 MiB)
checksum: 660ed86d6086dddf00716718d1ece340f1fb16fa73ffb635f427585ad01bdc52 (sha256)
- zipalign verified
- signature verified [v1, v2, v3]
Subject: CN=Android Debug, OU=Android, O=US, L=US, ST=US, C=US
SHA256: 1e08a903aef9c3a721510b64ec764d01d3d094eb954161b62544ea8f187b5953 / SHA256withRSA
Expires: Thu Mar 10 22:10:05 EET 2044
[Mon Apr 24 07:21:59 EEST 2023][v1.2.1]
Successfully processed 1 APKs and 0 errors in 1.16 seconds.
Signing process was successful
As seen above, when rebuilding the InsecureBankv2.apk the APKLab first uses the apktool_2.7.0.jar with the provided options
--use-aapt2: AAPT2 (Android Asset Packaging Tool) is a build tool used to compile and package the applications’s resources. AAPT2 parses, indexes, and compiles the resources into a binary format that is optimized for the Android platform.--debug: Sets android:debuggable to “true” in the APK’s compiled manifest--force-all: Overwrites existing files during build, reassembling the resources.arsc file and dex file(s)
Then, after rebuilding the InsecureBankv2.apk, as also shown at the output above, the uber-apk-signer-1.2.1.jar used by the APKLab in order to resign the APK. Android requires that all APKs be digitally signed with a certificate before they are installed on a device or updated.
At this point, and when the rebuilding and resigning process finish, a new folder should appear at the treeview of the decompiled application which contains the updated InsecureBankv2.apk as seen below.
InsecureBankv2/dist └── InsecureBankv2.apk
The newly created APK should be easily installed inside an android emulator or an android device. For the purposes of this lab the AVD manager VSCode plugin will be used in order to install and create the emulator.
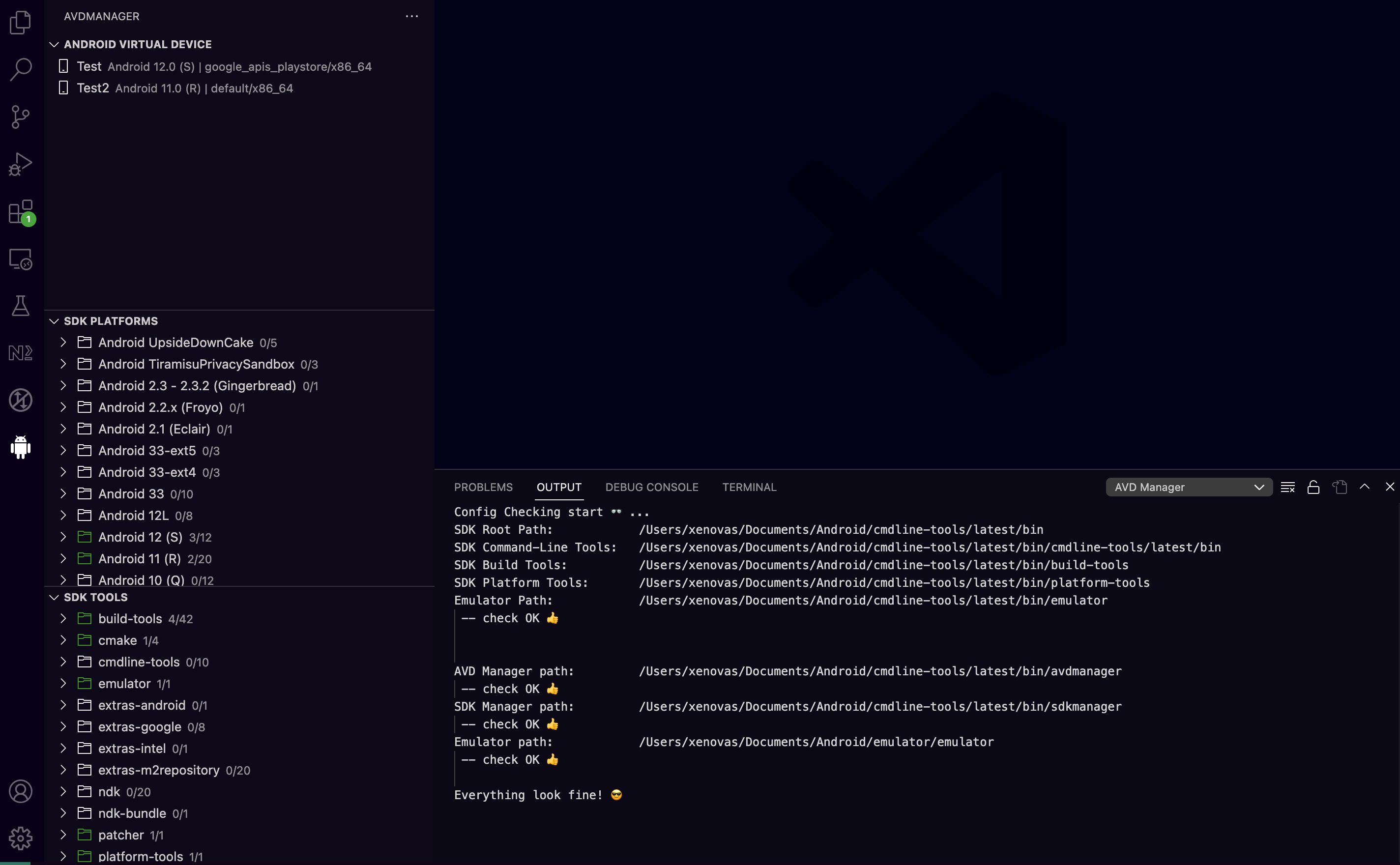
Ofcourse other emulators should also work such as genymotion, but as mentioned, this lab describes the "All in one setup" in VSCode. Moreover, because this lab is focused mainly on the debuging setup we will not go into great details of how to install and configure the virtual devices and Android SDK through the AVD Manager plugin. Nevertheless, the following screenshot shows a preview regarding the AVD Manager setup as seen at the output tab on VSCode
In sort, the following configuration / installations should be performed in order to use the AVD Manager
SDK Command-Line Tools SDK Build Tools SDK Platform Tools Emulator
From the SDK tools panel on AVD Manager plugin, the SDK platform tools version 34.0.1 will be installed, and then from the SDK platforms panel, the Android 11 (R) image with x86_64 ABI and Android SDK platform 30 will also be installed. Moreover, using the SDK tools we will install the android emulator version 32.1.12. Then we will start the emulator as follows
cd < Android folder > / emulator ./emulator -writable-system -avd < emulator name >
Furthermore, the adelphes android debugger plugin will be also be installed in VSCode IDE. This plugin allows developers to install, launch and debug Android applications from within the VSCode environment.
From VSCode IDE on the menu bar on the left we will select the "Run and Debug" button. From there, the "Add Configuration" option will be selected listed at the dropdown menu. Then, there will be two options to select regarding the Android configuration. The first should be the Android: Attach to Process and the second should be the Android: Launch Application.
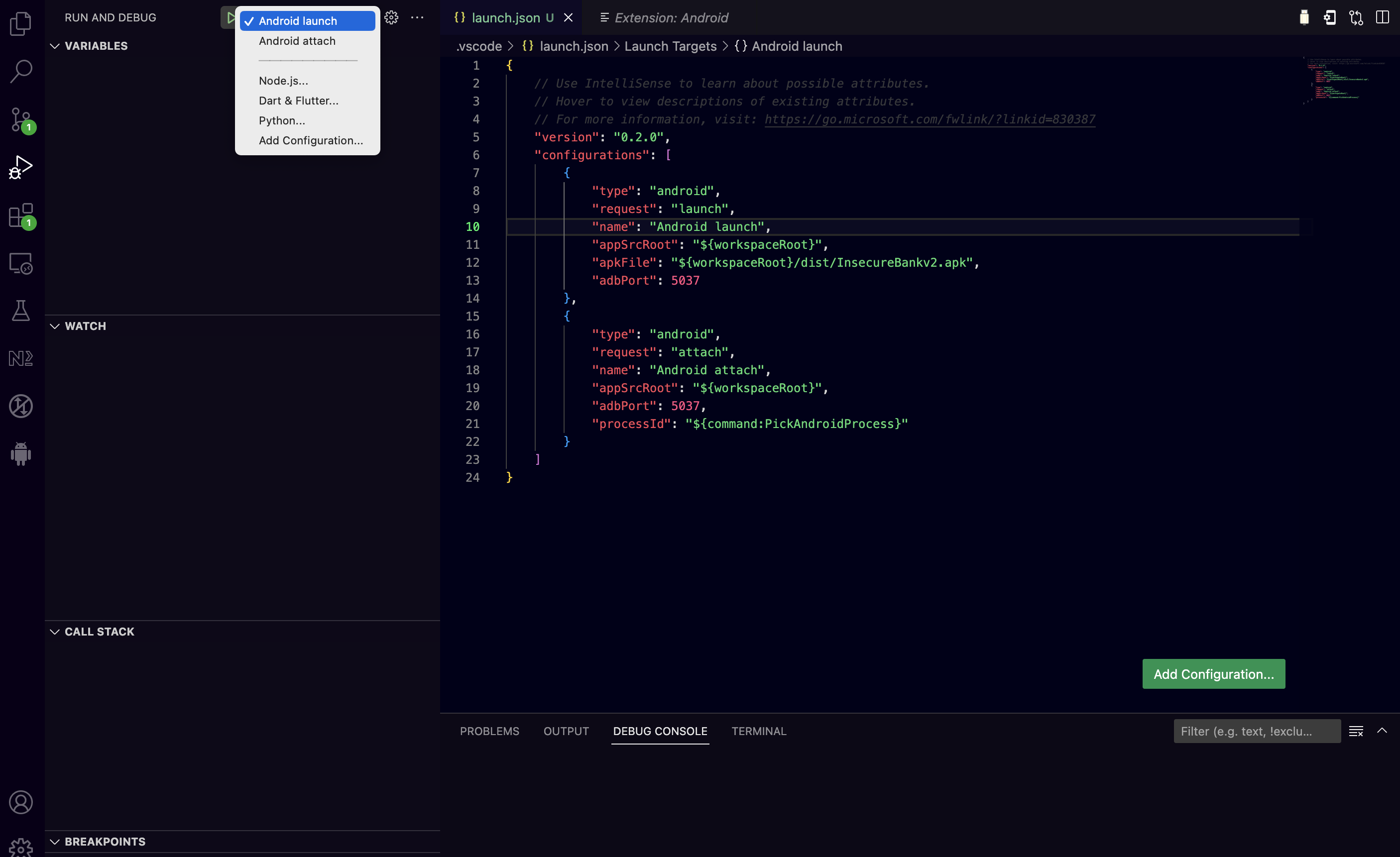
We can choose both and after some modifications the launch.json file should as be as follows.
{
"version": "0.2.0",
"configurations": [
{
"type": "android",
"request": "launch",
"name": "Android launch",
"appSrcRoot": "${workspaceRoot}",
"apkFile": "${workspaceRoot}/dist/InsecureBankv2.apk",
"adbPort": 5037
},
{
"type": "android",
"request": "attach",
"name": "Android attach",
"appSrcRoot": "${workspaceRoot}",
"adbPort": 5037,
"processId": "${command:PickAndroidProcess}"
}
]
}
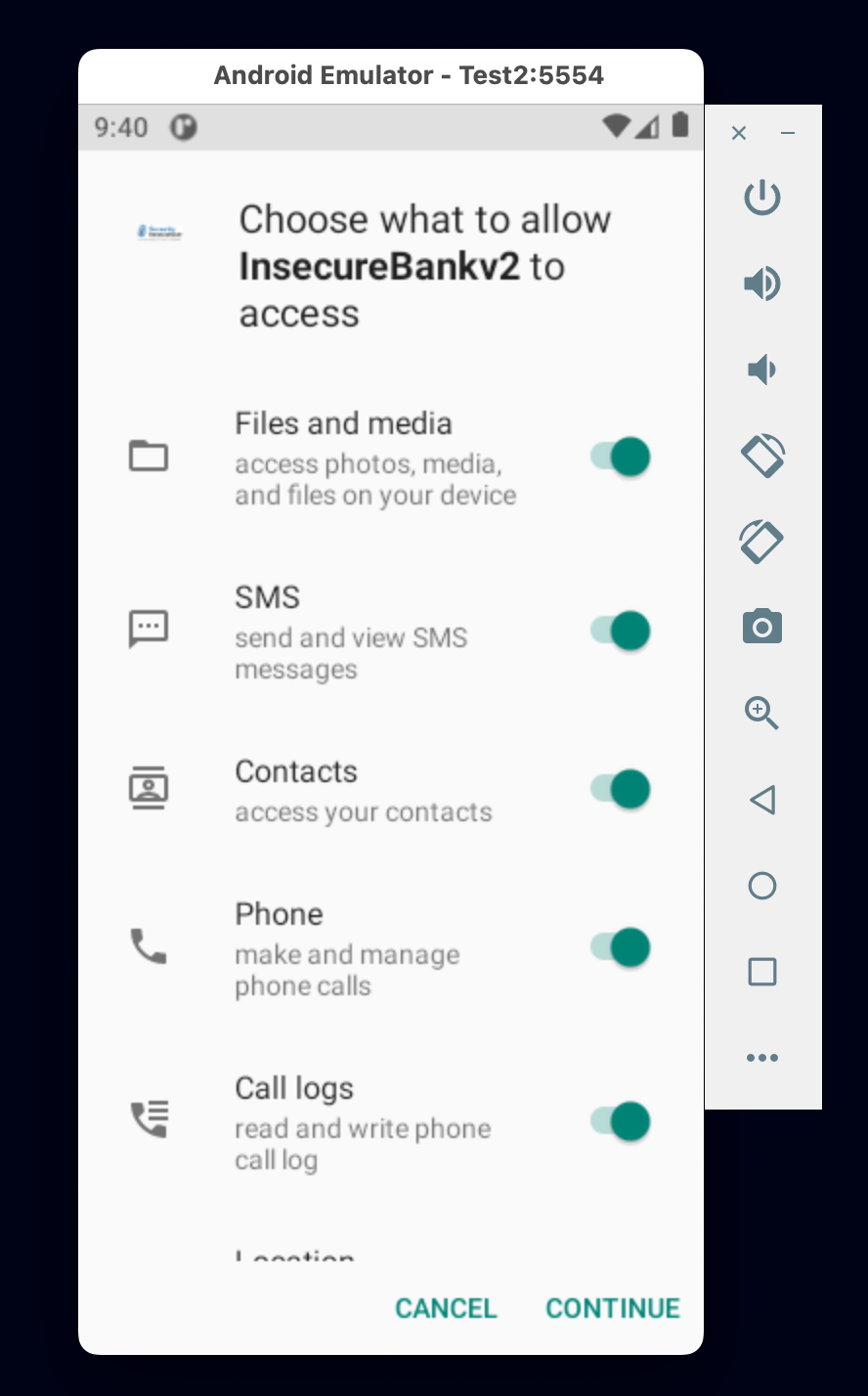
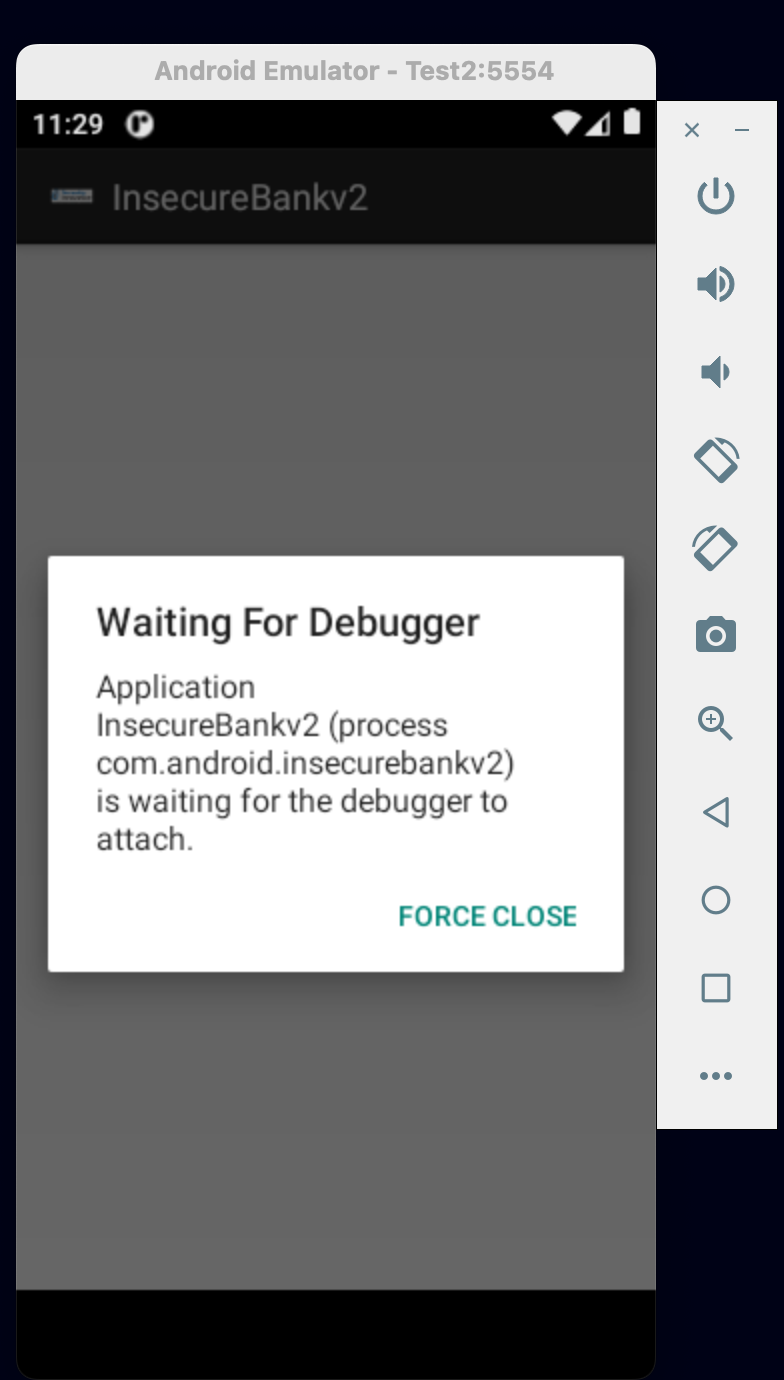
After we choose the Android: Launch Application from the dropdown menu, the application will automatically be installed inside the android emulator. Nevertheless, other installation options could be used such as using adb command or just drag and drop the APK into the emulator. The following screen will be shown at the emulator while running the application through VSCode IDE in debug mode.
Now, choose continue and then the following screen should be shown
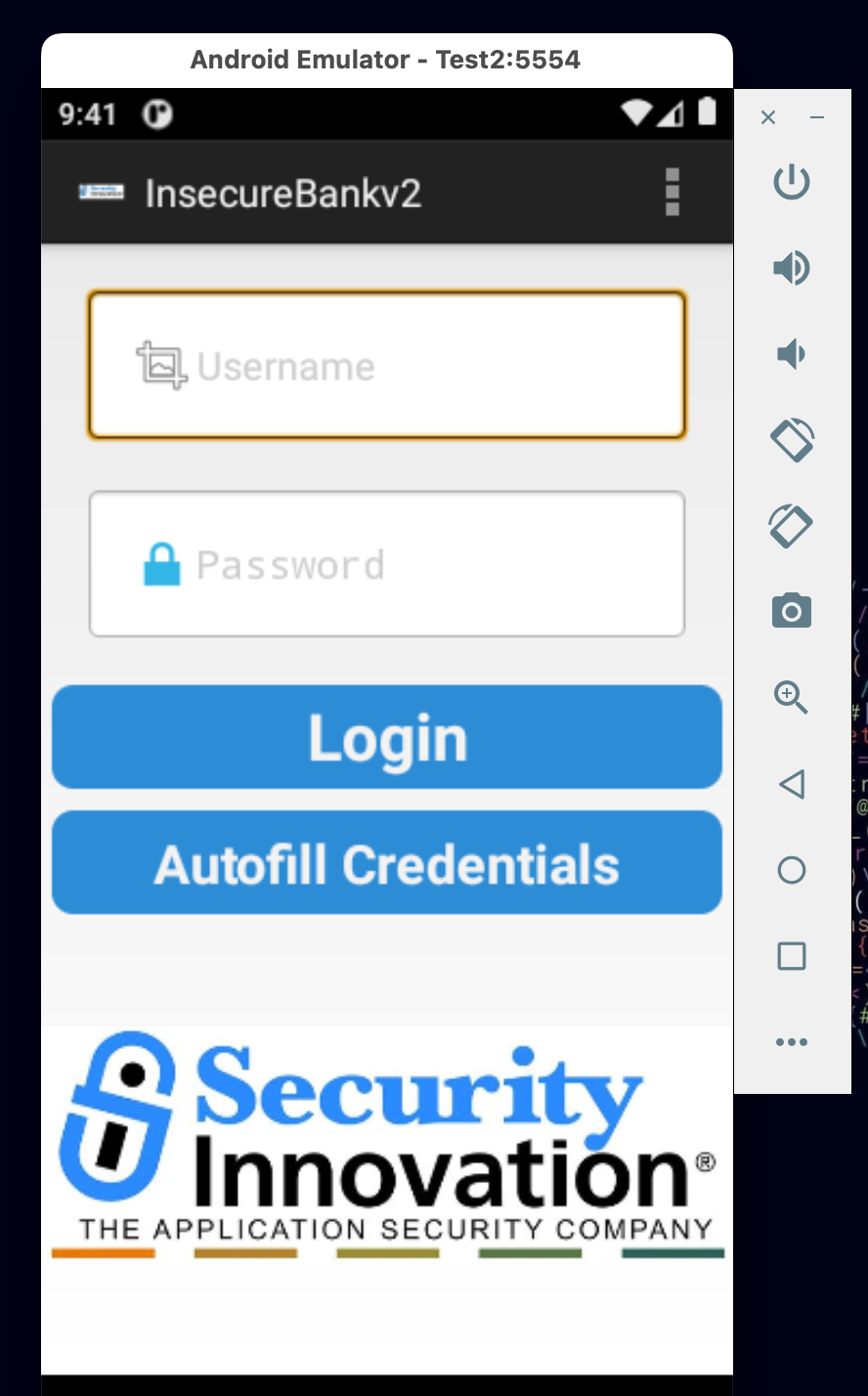
Now restart the debugger and after a while the application's login screen will show up.
At this point we should be able to add breakpoins into the code, but before we do this we should close everything in VSCode including the debugger, and then we will change the application's folder name into source. Then we will do the same at the java_src folder and we will rename it to src. Afterwards, the new structure of the decompiled application will be as follows
source ├── AndroidManifest.xml ├── apktool.yml ├── build ├── dist ├── original ├── res ├── smali └── src
Afterwards, we will start a new instance of VSCode and we will open the source folder using the following command
code a source
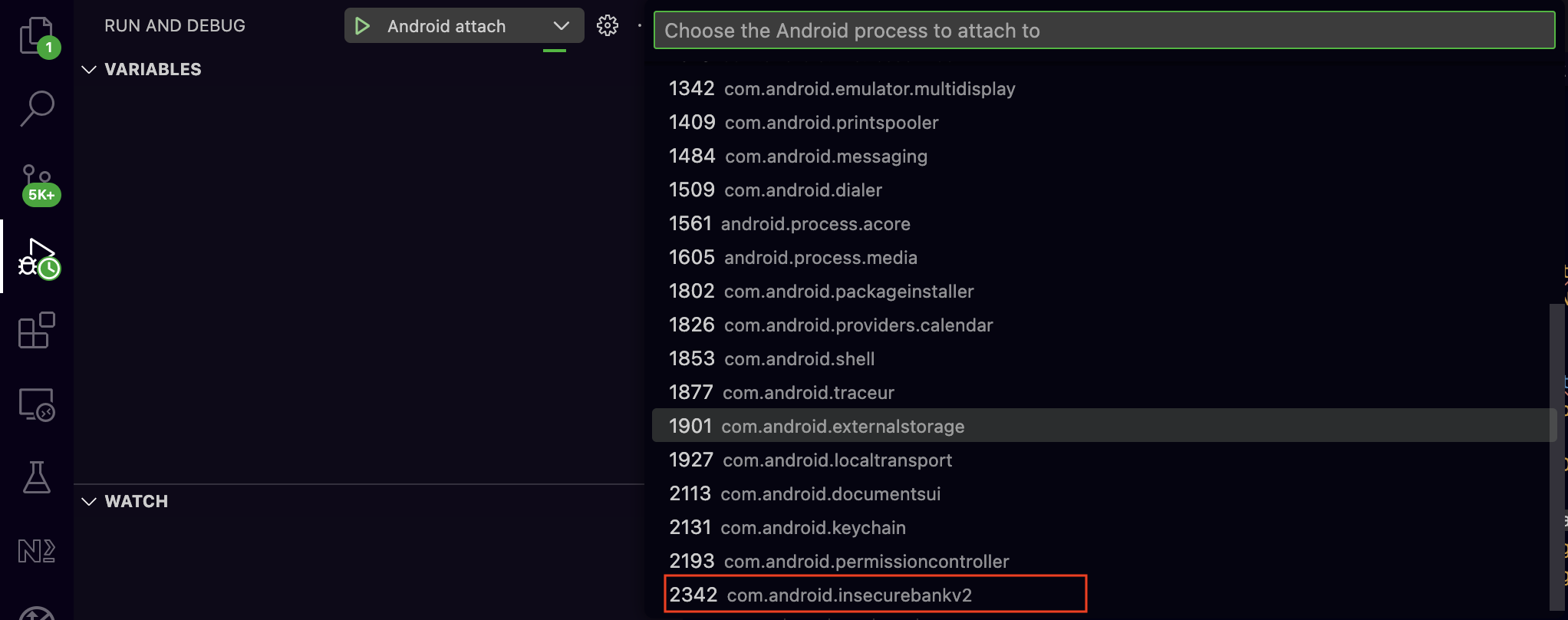
From the emulator we will start the InsecureBankV2 application and from the Run and Debug in VSCode we will choose the Android attach option from the dropdown menu in order to attach to a running process of the InsecureBankV2 app.
Now that we found the process we want to debug we will also check into the relevant folder as seen at the structure below for code related with the login functionality in order to put a breakpoint inside a function of our choice
source/src/com/android/insecurebankv2 ├── BuildConfig.java ├── C0238R.java ├── ChangePassword.java ├── CryptoClass.java ├── DoLogin.java ├── DoTransfer.java ├── FilePrefActivity.java ├── LoginActivity.java ├── MyBroadCastReceiver.java ├── MyWebViewClient.java ├── PostLogin.java ├── TrackUserContentProvider.java ├── ViewStatement.java └── WrongLogin.java
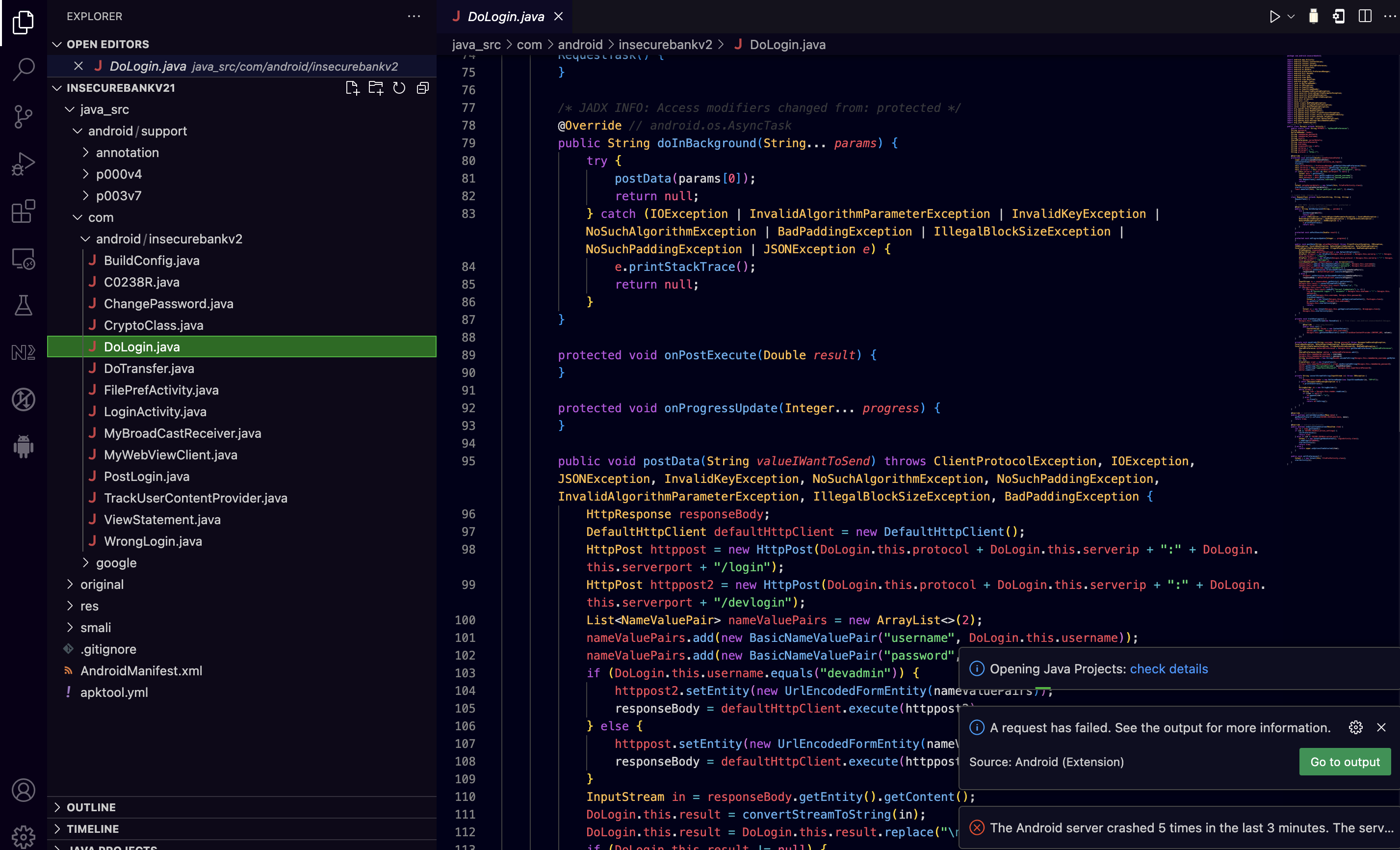
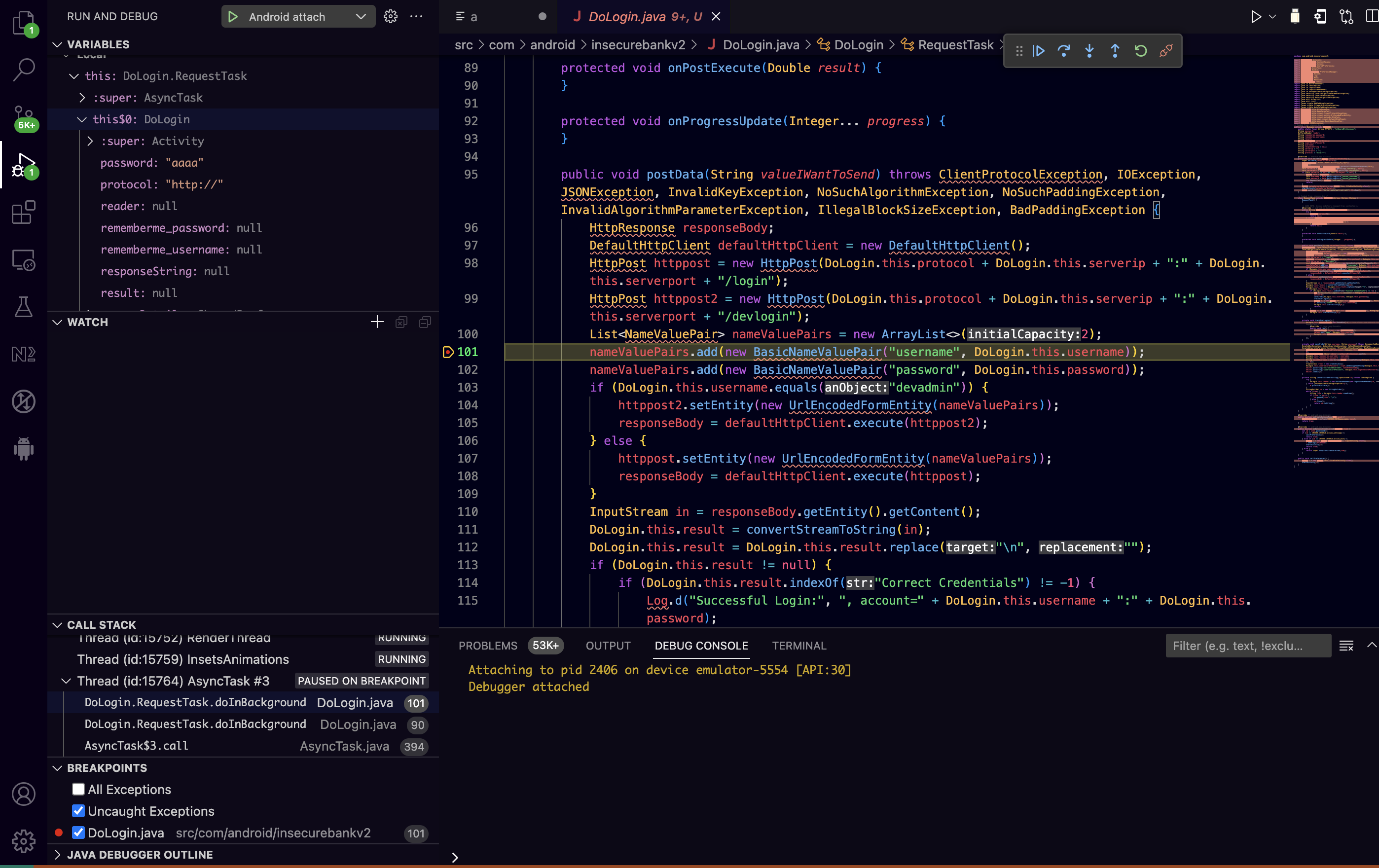
As seen above there are four .java files and as their names suggest they are closely related with the Login functionality. Then, we can examine the code of the .java files related with the Login functionality for security issues. For the purposes of this demonstration we will put a breakpoint into the DoLogin.java file at the postData() function at line 101. If we now put a username and password of our choice and press the login button we will have our hit! Now we can step into the code and check the values of the variables at the left pane on VSCode IDE.
Also as seen above, at the left pane of the VSCode IDE we have the variables, the call stack as well as the breakpoints listed, so we can examine the values, the function calls and the locations of our breakpoints into the code base. Thats it for now and i wish you happy bug hunting !